New Adobe Illustrator Patches Address Multiple Zero Day Vulnerabilities Discovered by FortiGuard Labs | FortiGuard Labs

Cisco Adaptive Security Appliance Software and Firepower Threat Defense Software for Firepower 2100 Series Appliances SSL/TLS Denial of Service Vulnerability
What are the potential consequences of zero-day attacks?
Zero-day attacks can have severe consequences for both organizations and individuals. One potential consequence is data breaches, where attackers gain unauthorized access to sensitive information. This can lead to financial losses, reputational damage, and legal consequences. Another consequence is the disruption of critical systems and services. By exploiting zero-day vulnerabilities, attackers can take control of systems and networks, causing downtime, operational disruptions, and even impacting public services. Furthermore, zero-day attacks can be used for espionage purposes. Hackers can infiltrate organizations to steal valuable intellectual property, trade secrets, or government secrets, compromising national security. Lastly, zero-day attacks can also be a stepping stone for larger and more sophisticated cyber attacks, allowing attackers to gain a foothold in a system and further exploit vulnerabilities.
What steps can organizations take to mitigate the risks associated with zero-day vulnerabilities?
Organizations can take several steps to mitigate the risks associated with zero-day vulnerabilities. First and foremost, keeping software and operating systems up to date is crucial. Developers often release patches and updates to address known vulnerabilities, and promptly applying these updates can help protect against zero-day exploits. Additionally, implementing a layered defense strategy is essential. This includes using firewalls, intrusion detection and prevention systems, and antivirus software to detect and block malicious activities. Employing threat intelligence tools and services can also provide real-time information about emerging threats and zero-day exploits, enabling organizations to take proactive measures. Conducting regular vulnerability assessments and penetration testing can help identify weaknesses and prioritize security measures. Another step organizations can take is to adopt zero-trust security principles, where every user and device is treated as potentially compromised, and access to resources is granted based on continuous authentication and verification. Lastly, having an incident response plan in place can help organizations effectively respond to and mitigate the impact of zero-day attacks.
How can cybersecurity consultants like Securicon assist in addressing the threat of zero-day vulnerabilities?
Cybersecurity consultants, like Securicon, play a crucial role in addressing the threat of zero-day vulnerabilities. These consultants have in-depth expertise and knowledge of the latest cyber threats and attack techniques, including zero-day exploits. They can conduct comprehensive vulnerability assessments, penetration testing, and security audits to identify potential vulnerabilities and risks within an organization’s systems and infrastructure. By leveraging their expertise, consultants can provide recommendations and guidance on implementing effective security controls and best practices to mitigate the risks associated with zero-day vulnerabilities. Additionally, cybersecurity consultants can assist organizations in developing incident response plans, ensuring they have the necessary processes and procedures in place to detect, respond to, and recover from zero-day attacks. Consultants can also provide employee training and awareness programs to educate personnel about the risks of zero-day attacks and how to practice good cyber hygiene. Overall, cybersecurity consultants serve as strategic partners in helping organizations enhance their security posture and protect against the evolving threat landscape, including zero-day vulnerabilities.
Full summary
The digital world is facing a growing threat from zero-day vulnerabilities, with cyber attackers exploiting undisclosed flaws in software and systems before developers can patch them. These zero-day exploits, which allow hackers to launch targeted attacks with a high likelihood of success, have become a favorite tool for cybercriminals, hacktivists, corporate espionage agents, and even nation-state actors.
Zero-day vulnerabilities, by definition, are unknown to software vendors until they are discovered and exploited by attackers. This puts organizations and individuals at risk as they are unable to implement protective measures before the vulnerabilities are targeted. Once a zero-day vulnerability is discovered, developers work to quickly create patches and updates to address the issue. However, not all users promptly apply these patches, leaving their systems exposed to potential attacks.
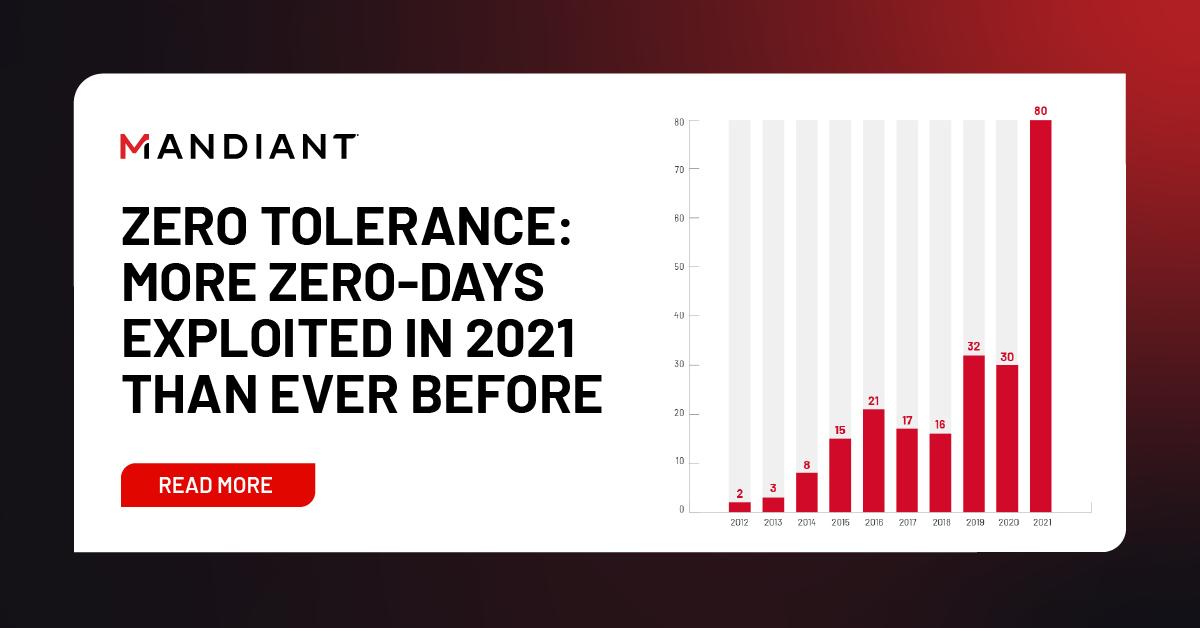
The number of zero-day exploits is increasing year by year, reflecting the growing sophistication of cyber attackers. According to research by Mandiant, the number of zero-days doubled between 2019 and 2021. These vulnerabilities can target various systems and applications, including operating systems, web browsers, office software, open-source components, hardware, firmware, and even IoT devices.
Both targeted and non-targeted zero-day attacks pose significant risks. Targeted zero-day attacks typically focus on large organizations, government agencies, and high-profile individuals. These attacks can have devastating consequences, including data breaches, financial losses, and even national security threats. Non-targeted attacks, on the other hand, can affect any user of a vulnerable system, leading to identity theft, cybercrime, and other forms of damage.
Detecting and mitigating zero-day vulnerabilities and exploits is a complex task. Organizations can take several proactive steps, such as implementing threat detection systems, egress filtering, network visibility, device oversight, and third-party vendor management. Adopting a zero-trust security paradigm, conducting regular vulnerability assessments, and keeping software and operating systems up to date are also crucial.
To address the evolving threat landscape, organizations can seek assistance from cybersecurity consultants like Securicon. With a team of experienced professionals from the U.S security community, including experts from the Department of Defense, Department of Homeland Security, and the U.S Cyber Command, Securicon can help identify and mitigate the risks associated with zero-day vulnerabilities.
In conclusion, the rise of zero-day vulnerabilities presents a significant menace in the digital world. These undisclosed flaws in software and systems empower cyber attackers to exploit vulnerabilities before developers can patch them. As the threat grows, organizations and individuals must remain vigilant, prioritize timely patching and updates, and leverage the expertise of cybersecurity professionals to protect against these sophisticated and elusive attacks.